
Brave
Brave Browser is a Chromium fork with many interesting features not found elsewhere, such as built-in Adblock and other extensions, fingerprinting protection, a cleaner Preferences menu compared to other Chrome forks, and the (opt-in) ability to automatically support (pay) the websites you visit. The developers describe it as "A browser with your interests at heart."[1] with the built-in privacy protections.
Spyware Level: High
Brave is self updating software, uses Google as the default search engine, has built-in analytics, and even has an opt out rss-like news feed similar to Firefox's pocket feature. These features aren't the first things that come to mind when I imagine a privacy oriented browser.
Whitelisting spyware from Facebook and Twitter
On its website, Brave claims that "Brave fights malware and prevents tracking, keeping your information safe and secure. It’s our top priority."[6]. Yet despite this claim, Brave actually disables its tracking protections for Facebook and Twitter's scripts that allow them to track people across the web.[5] Brave has been actively downplaying the role that JavaScript plays when tracking someone.
"Loading a script from an edge-cache does not track a user without third-party cookies or equivalent browser-local storage, which Brave always blocks and always will block. In other words, sending requests and receiving responses without cookies or other means of identifying users does not necessarily create a tracking threat."[7]
This couldn't be more far from the truth. Just because a website isn't able to store cookies, doesn't mean it can't uniquely identify you. Using JavaScript from Facebook and Twitter would be more than enough to track you and blocking cookies alone isn't going to stop that. Just as a quick point of reference to what information JavaScript can scrape, you might want to visit this.
They later on added an option to the extension to disable all of the JavaScript, but this new feature seems to be nothing more than the JavaScript switch found in vanilla Chromium.
A quick note on the whitelisting trackers: This specific point on whitelisting trackers isn't making the case of Brave being spyware as much as showing Brave's privacy features being snake oil.
Auto-updates
Brave will check for updates every time you run it, and you can't turn it off from the browser. Athough, it's on Brave's low priority list to add an option to do so[2]. I say low priority because it's been over a year and it hasn't been implemented yet.
A special note is that on most (all?) GNU/Linux distributions, the automatic updates are only for the extensions.
Anti-privacy search engine by default
Google is the default search engine of Brave. For a browser that claims to be privacy oriented, this is a red flag. They at least make it easy for you to change the default search engine on the first run.
Brave has built-in telemetry
While running, Brave will make lots of requests to the domain p3a.brave.com as telemetry. They claim they store the collected data for several days[8]. Telemetry is the last thing that comes to mind when I imagine a privacy oriented browser.
Brave Today
Brave now has new feature similar to Firefox's pocket called Brave Today. If you don't know what Firefox Pocket is, it's basically an rss-like news feed is shown in every blank tab. This feature Brave has is sadly an opt-out rather than an opt-in and sends lots of requests to Brave's servers.
SafeBrowsing
Brave uses SafeBrowsing. It's a feature that tries to "protect" the user from potentially unsafe websites. However, it sends requests to fetch the information required to do so. Judging by some of the information in Miscellaneous requests, I wouldn't put it past Brave to use Google's SafeBrowsing implementation rather than their own.
Brave Rewards
Brave has a rewards program. You can find more information about it here[3]. At first glance it looks like the rewards program is an opt in, but the browser makes connections to these domains regardless if you sign up or not:
rewards.brave.com
api.rewards.brave.com
grant.rewards.brave.com
Miscellaneous requests
Brave on first run sends a request to fetch the library used for checking spelling errors:

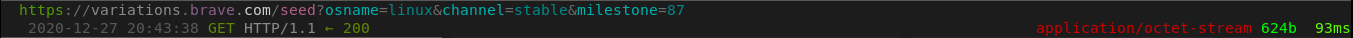
Brave on first run sends a request to variations.brave.com, which if I had to give a guess, has to do with some way to verify affiliates:
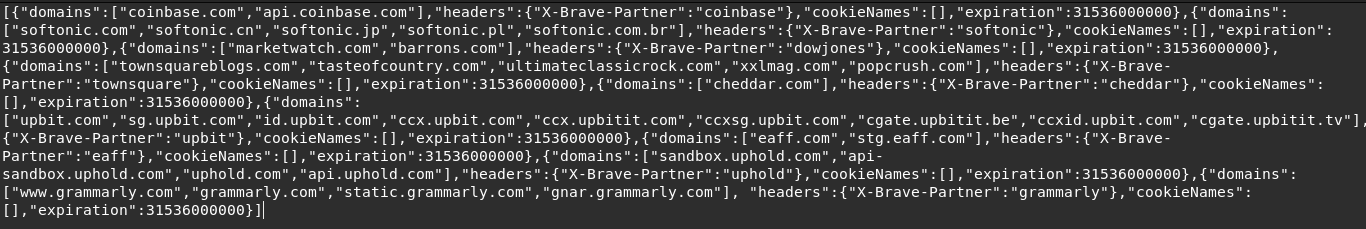
Right after the request to variations.brave.com is made, Brave fetches the list of affiliates through laptop-updates.brave.com[4]:
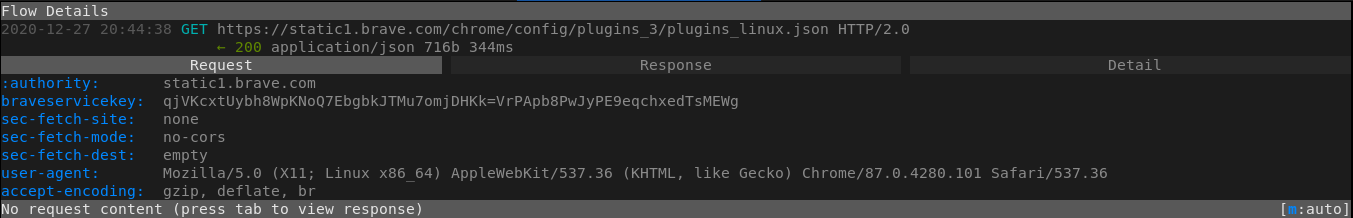
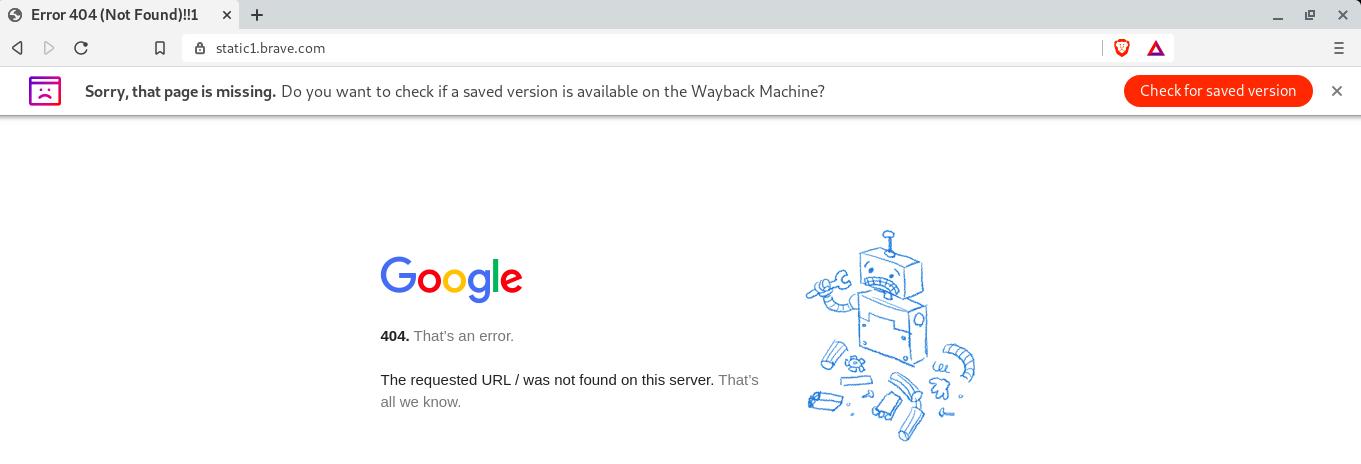
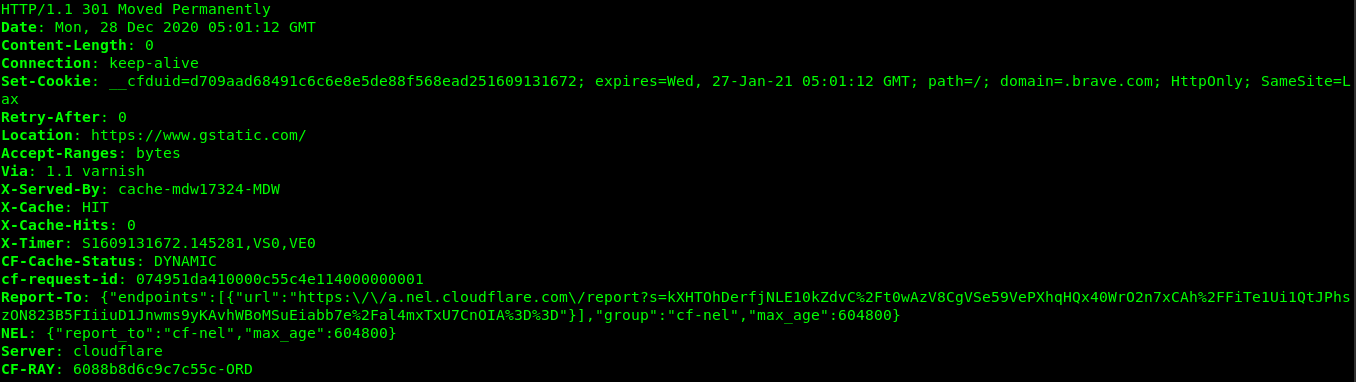
Brave made a request to static1.brave.com, which looks like it's used to fetch plugin information? When I entered the url into the browser to explore, it redirected to Google's error 404 page[9]. This seems kind of unsettling to me that one of Brave's domains would do this:
I decided to do curl --head static1.brave.com, and I wasn't pleased with the results. It appears Brave uses Google's gstatic:
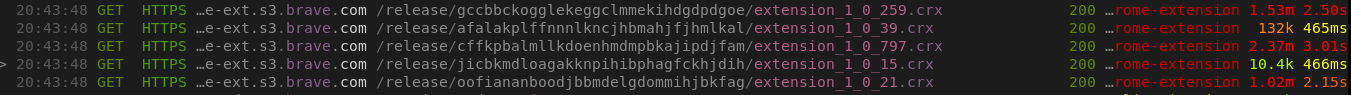
On the first run, Brave fetches five extensions from brave-core-ext.s3.brave.com and tries to install them:
Sources
1. Brave's website [web.archive.org]
2. Add a disable autoupdate feature [web.archive.org]
3. Brave Rewards Program [web.archive.org]
4. Laptop Headers [web.archive.org]
5. Facebook, Twitter Trackers Whitelisted by Brave Browser [web.archive.org]
6. Brave Browser Features [web.archive.org]
7. Script Blocking Exceptions Update [web.archive.org]
8. Brave's Analytics [web.archive.org]
9. Brave's static site [archive.is]
This article was created on 5/7/2018
This article was last edited on 12/30/2020
If you want to contribute to this website, you can always make a pull request.
All contributions must be licensed under the CC0 license to be accepted.
